An In-Depth Look at Different SSL Certificate Types


Intro
In today’s interconnected world, where virtually every interaction occurs in the digital realm, cybersecurity holds a central role in safeguarding our personal and professional lives. The convergence of cybersecurity and network security isn’t merely an afterthought; it’s a necessity. As our devices become more connected than ever, ensuring the protection of data and networks becomes paramount.
Overview of the significance of cybersecurity in today's interconnected world
Cybersecurity has evolved into a multi-faceted discipline involving technical, operational, and managerial practices to protect networks from unauthorized access or attacks. The consequences of lapses in security can be dire—ranging from financial loss to compromised personal information. Statistics tell a telling tale: in 2022 alone, data breaches affected millions, highlighting vulnerabilities in even the most robust systems.
Digital communication is like a bustling highway, with SSL certificates serving as road signs that ensure data travels safely to its destination. SSL, or Secure Socket Layer, enhances the security of connections between web browsers and servers. It’s crucial for anyone operating online, ensuring that sensitive information remains confidential and secure.
Evolution of networking and security convergence
As technology progressed, so too did the threats that challenge it. No longer can organizations merely rely on traditional perimeter defenses. Today, security is an organization-wide initiative that requires collaboration between departments and specialized teams. The melding of cybersecurity and network security represents a shift toward a comprehensive approach that integrates endpoints, cloud services, and traditional networks.
Networking security has stepped up its game with better encryption, real-time monitoring, and advanced intrusion detection systems. It’s not only about protecting the network but also about fostering trust—trust that the communication between a user and a website is secure. SSL certificates provide this trust by verifying the legitimacy of entities that exchange sensitive information.
Moreover, as we delve deeper into the varieties of SSL certificates in the forthcoming sections, we’ll uncover how they play an integral role in this security paradigm. Their classification, functionalities, and implementations give us a better understanding of how to strengthen digital communications and ultimately protect the entire ecosystem.
Preamble to SSL Certificates
In the ever-evolving digital landscape, ensuring secure communications is paramount. That’s where SSL (Secure Sockets Layer) certificates enter the fray, acting as the gatekeepers to secure online transactions, protecting sensitive information from prying eyes. This section aims to shed light on the significance of SSL certificates while also framing the context for the subsequent parts of this article.
Understanding SSL Technology
At its core, SSL technology is all about encryption. When you access a website with an SSL certificate, a handshake occurs between your browser and the web server. During this handshake, they agree on encryption protocols, ensuring that any data exchanged remains confidential. Think about it as sending a letter in a locked box; only the recipient has the key.
With HTTPS (HyperText Transfer Protocol Secure) now being a standard requirement for websites, particularly those handling sensitive data, understanding the underpinnings of SSL becomes crucial. SSL not only encrypts data but also authenticates the identity of the website, allowing users to ensure they're indeed communicating with the intended entity. This dual function of ensuring confidentiality and authenticity is what makes SSL technology indispensable for modern web safety.
Purpose and Importance of SSL Certificates
The purpose of SSL certificates extends far beyond mere encryption. They serve as a vital element in building trust between a website and its users. When visitors see that a site is secured with SSL, it not only assures them that their data is safeguarded but also reinforces the site's credibility. This trust translates to better user experience and often leads to increased conversions, especially for e-commerce sites.
Key benefits of SSL certificates include:
- Data Protection: SSL certificates encrypt sensitive information, like credit card numbers and personal details, during transmission.
- Improved SEO Rankings: Search engines like Google favor HTTPS websites, giving them higher visibility in search results.
- Trust Indicators: Just seeing the padlock symbol in the URL bar can greatly reduce user anxiety, influencing their decision to engage with the site.
- Regulatory Compliance: Many industries require encryption to protect consumer data, and having an SSL certificate can help meet compliance standards.
SSL certificates are more than just a technical specification; they are the bedrock of trust in the digital ecosystem.
In essence, this section sets the stage for a deeper exploration of the various types of SSL certificates that will be discussed later. Each type comes with its own set of features and benefits that address specific needs across different sectors. As we advance, we will dissect these categories to fully appreciate their roles in fortifying web security.
Types of SSL Certificates
In the realm of cybersecurity, understanding the different types of SSL certificates is crucial. These certificates not only signify trustworthiness but also play a pivotal role in data protection during online transactions. With the growing concerns around data breaches and cyber attacks, choosing the right type of SSL certificate can be a game changer for both businesses and their clients. In this section, we will dissect the various types of SSL certificates, paying close attention to their features, benefits, and considerations.
Domain Validated Certificates
Domain Validated (DV) certificates are the simplest form of SSL certificates. Obtaining them is relatively straightforward, primarily because the validation process only requires the applicant to prove ownership of the domain. The certificate authority will send an email to the registered domain owner, and once validated, the certificate is issued. This type of SSL is ideal for small websites or personal blogs that need some level of encryption but are not handling sensitive user data.
Benefits of Domain Validated Certificates:
- Easy and quick issuance.
- Cost-effective; often available for free from various providers.
- Basic encryption ensures a minimal level of security.
Organization Validated Certificates


Organization Validated (OV) certificates are a step up from DV certificates. The validation process involves a more rigorous examination whereby the certificate authority verifies the legitimacy of the organization behind the domain. This entails checking the business' registration documents and its operational status. OV certificates cater to businesses that want to establish more trust with their clients without going through the extensive process associated with extended validation.
Considerations for Organization Validated Certificates:
- Requires more documentation than DV certificates.
- Suitable for businesses that handle user information and want to instill a sense of trust.
- Generally more expensive than DV certificates due to additional verification steps.
Extended Validation Certificates
Extended Validation (EV) certificates take the validation process a step further. They provide the highest level of authentication among SSL certificates. The main aim here is to verify the legal identity of the organization so that visitors can trust that they are dealing with a legitimate business. The browser displays a green address bar along with the organization's name and other identifying information, which signals to users that they are on a secure site.
Key Features of Extended Validation Certificates:
- Comprehensive validation process that includes legal and operational checks.
- Prominently visible identity indicators that enhance user trust.
- Ideal for e-commerce sites and online services that process sensitive transactional data.
Wildcard Certificates
Wildcard certificates are designed for websites that need to secure multiple subdomains with a single SSL certificate. This is particularly useful for businesses that have numerous subdomains under a primary domain. For instance, if your primary domain is , a wildcard certificate can secure , , and others under this umbrella.
Advantages of Wildcard Certificates:
- Cost-effective solution for multiple subdomains.
- Simplified management, as only one certificate needs renewal.
- Reduces confusion and enhances coherence for users visiting different sections of the website.
Multi-Domain Certificates
As the name suggests, Multi-Domain certificates are ideal for securing multiple different domains under a single SSL certificate. This can be a major time-saver for companies managing several brands or services online. Whether it's , , or , this type of certificate caters to varied domains efficiently in one package.
Considerations for Multi-Domain Certificates:
- Flexibility to secure various types of domains.
- Potentially higher cost than single-domain certificates due to its scope.
- Ease of management by consolidating several certificates into one.
The classification of SSL certificates into these four types articulates the diverse needs of businesses. Each type serves a distinct purpose, yet all contribute immensely to ensuring online security and trust. Careful consideration of these options goes a long way in implementing effective online security measures.
Comparative Analysis of SSL Certificate Types
In today's digital landscape, the plethora of SSL certificate types presents both opportunity and challenge for organizations. Understanding the nuances between these certificates is more than just a technical exercise; it's about decision-making that influences security posture and trustworthiness. The comparative analysis of SSL certificate types sheds light on their distinct attributes, weighing costs against benefits, assessing security enhancements, and matching solutions to business needs.
Cost vs. Benefit Analysis
When it comes to investments in cybersecurity, every penny counts. SSL certificates are no exception. The prices vary considerably based on the type chosen, driving home the point that one-size-fits-all is rarely a winning strategy. For example, Domain Validated (DV) certificates can be as inexpensive as a cup of coffee, appealing to startups and personal sites.
On the other hand, Wildcard and Extended Validation (EV) certificates come with a heftier price tag but can offer significant advantages. These higher-tier certificates often ensure a more robust trust signal to visitors. Here’s a snapshot:
- Domain Validated Certificates (DV):
- Organization Validated Certificates (OV):
- Extended Validation Certificates (EV):
- Cost: Low
- Benefit: Quick issuance, suitable for smaller sites.
- Cost: Moderate
- Benefit: Offers a good balance of trust and affordability.
- Cost: High
- Benefit: Provides maximum trust and typically displayed as a green address bar in the browser.
While lower-cost options may seem appealing, businesses wary of phishing attacks might find the investment in EV certificates justified in fostering consumer confidence. Evaluating return on investment is crucial in making the right call.
Security Enhancements Across Certificate Types
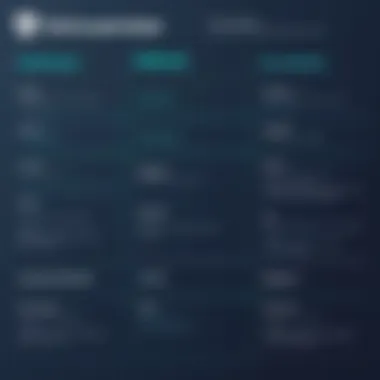
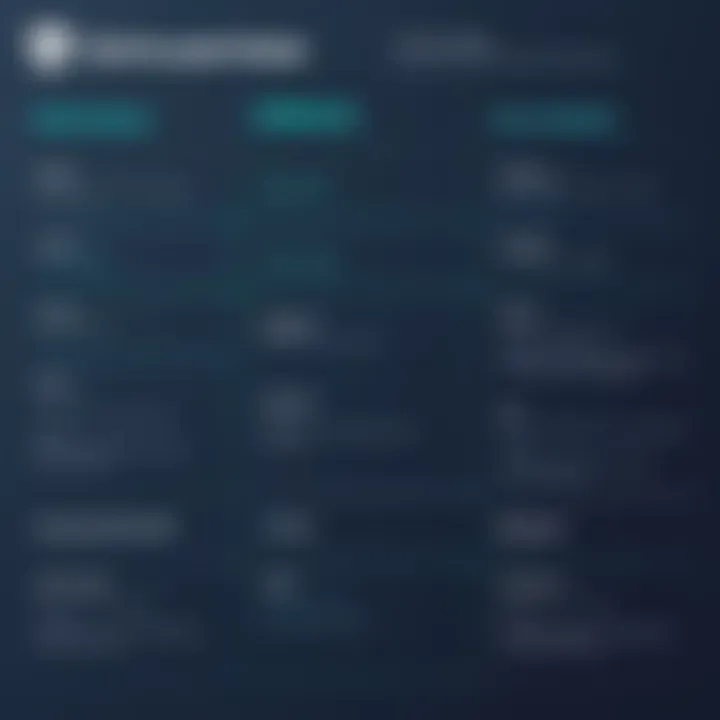
Security can feel like a double-edged sword at times. Not all SSL certificates provide the same level of assurance. For instance, while a DV certificate confirms ownership of a domain, it doesn’t verify the identity of the business. Consumers might be wary of sharing sensitive information if they don’t see that extra layer of verification.
- Organization Validated Certificates (OV): These add a layer of verification by confirming the organization’s identity, significantly reducing the chances of impersonation.
- Extended Validation Certificates (EV): The reigning champion of trust, EVs go the extra mile, offering rigorous vetting of the organization. The green address bar acts as a beacon for potential customers, solidifying the trust factor.
Selecting an SSL certificate isn’t merely about protection—it’s also about signaling security to potential clients. Thus, understanding the distinct enhancements provided across certificate types plays a crucial role in the decision-making process.
Suitability for Different Business Needs
Businesses differ as much as their needs, and SSL certificates must be aligned accordingly. E-commerce sites, for instance, cannot afford to compromise on security and typically opt for EV certificates to protect customer transactions and boost credibility.
Consider the following factors when matching SSL types to business needs:
- Nature of Business:
- Expected Traffic:
- Regulatory Standards:
- Small blogs might find DV certificates adequate.
- An e-commerce site would benefit from an OV or EV certificate, creating trust in transactions.
- High-traffic websites would do well with Wildcard or Multi-Domain certificates to streamline security management.
- Some industries have strict compliance regulations requiring specific types of SSL certificates, influencing decisions heavily.
By aligning SSL choices with business strategy, organizations can make informed decisions that not only protect sensitive data but also enhance their professional reputation.
This analysis is meant to clarify the financial implications, the security advancements, and the unique business needs that dictate the choice of SSL certificates. Making educated decisions here can lead to substantial advantages.
SSL Certificate Management
SSL certificate management is a critical element in the realm of cybersecurity, particularly for organizations that prioritize the authenticity and security of their digital communications. In a world where cyber threats loom large, managing SSL certificates effectively can mean the difference between a secure website and an exposed vulnerability.
It's not merely a matter of acquiring an SSL certificate and hoping for the best. Organizations must continuously oversee their SSL infrastructure to ensure that every certificate is active, valid, and optimized for the highest level of security. This involves regular checks for expiration dates, ensuring proper installation, and addressing any configuration issues that may arise.
Best Practices for SSL Management
To maintain a robust SSL management strategy, it’s imperative to adhere to several best practices:
- Regular Audits: Conduct routine audits of your certificates. This helps identify expired, misconfigured, or redundant SSL certificates, ensuring that your digital assets remain secure.
- Centralized Management: Use a centralized management tool to streamline SSL certificate tracking. This reduces the risk of errors and helps in quick deployments and renewals.
- Keep an Inventory: Maintain an up-to-date inventory of all SSL certificates in use. Include relevant details like vendor information, expiration dates, and domains included.
- Automate Renewals: Whenever possible, automate the renewal process for SSL certificates. This ensures that certificates don’t lapse and minimizes administrative overhead.
- Educate Staff: Train IT staff about the importance of SSL certificates and proper management practices. Awareness helps in mitigating risks associated with human error.
"SSL management is not a one-off task; it's an ongoing commitment to security."
Monitoring and Renewal Processes
Monitoring SSL certificates is vital to ensure that the peace of mind that comes from having a secured site remains intact over time. Regular oversight means utilizing tools that can alert administrators well before certificates expire. Most organizations should strive for notifications days or weeks in advance of expiration dates.
When it comes to renewals, a comprehensive approach is key. Organizations must develop a clear process that includes:
- Setting Reminders: Establish reminders well in advance of certificate expiry—whether through calendar alerts or specialized management software.
- Reviewing Certification Needs: Before renewing, assess whether the current certificate meets your organization's needs. Adjust types accordingly, particularly if your site has expanded.
- Testing Renewed Certificates: After renewal, test the implemented certificate on your site. This includes checking for proper installation and ensuring that it does not cause any disruptions.
- Compliance Checks: If you're part of a regulated industry, ensure that your renewed certificates meet all compliance requirements.
Successfully managing SSL certificates not only enhances security but also builds trust with users. It's a foundational component of online credibility that ensures customer confidence in your digital presence.
Challenges and Limitations
Understanding the challenges and limitations associated with SSL certificates is crucial for anyone involved in cybersecurity, IT, or web management. While SSL certificates play a pivotal role in securing online communications, they are not without their pitfalls. Exploring these aspects is essential to ensure that businesses do not fall prey to common vulnerabilities and misconfigurations that can undermine the very protections these certificates are meant to provide.
Common Vulnerabilities Associated with SSL


SSL certificates, despite their robust nature, can expose systems to various vulnerabilities. A prevalent issue is the use of outdated cryptographic protocols. Many organizations still utilize SSL 3.0 or early TLS versions, which are susceptible to attacks like POODLE. Furthermore, the algorithm used for generating SSL certificates can also pose threats if weak ciphers are in play. This can open doors for attackers to decrypt sensitive data or perpetrate a man-in-the-middle attack.
Another significant vulnerability lies in the certificate lifecycle management. If certificates are not renewed on time or, worse, if expired certificates are left deployed, browsers will flag these as insecure, shaking user trust. Also, improper handling of private keys is a serious concern. If these keys are leaked, the security of all communications protected by that SSL certificate is compromised.
"The effectiveness of SSL certificates is proportionate to the diligence in managing their security. A lapse in vigilance can have dire consequences."
Misconfigurations and Their Risks
Misconfigurations are a common bane in the world of SSL certificates. Simple errors, such as failure to properly install the intermediate certificates, can lead to untrusted connections. This means users might receive warnings when trying to access websites, leading to a significant drop in traffic and trust.
Another risk often overlooked is the incorrect settings in the server's SSL/TLS configuration. For instance, using a weak certificate chain or improper redirect rules could expose the site to SSL stripping attacks, where attackers downgrade secure HTTPS connections to insecure HTTP.
Furthermore, there are systemic risks connected to expired SSL certificates. The consequences can range from service disruptions to loss of customer confidence. Even a few minutes of downtime can have financial repercussions, especially for e-commerce sites.
In summary, while SSL certificates are integral to digital security, the challenges and limitations they present require constant attention and expertise. Cybersecurity professionals need to not only implement these certificates but also actively manage and monitor them to mitigate risks.
Future Trends in SSL Technology
The digital landscape is ever-evolving, and so are the security measures that protect it. The importance of discussing the future trends in SSL technology cannot be overstated. As cyber threats continue to advance, SSL certificates must adapt to not only meet but exceed the expectations of security protocols. By exploring these trends, we can better understand how SSL technology will shape the way we secure our online communications in upcoming years.
Emerging Security Protocols
New security protocols are popping up like daisies in spring, each one aiming to fortify online defenses against a changing threat landscape. One notable trend is the increased adoption of TLS 1.3, which has been designed to enhance performance and security when compared to its predecessor, TLS 1.2. This newer protocol reduces the number of round trips needed for a handshake—meaning that connections are established faster, which is music to the ears of both users and website operators.
- Key Benefits of TLS 1.3:
- Enhanced Privacy: It encrypts more of the communication process, making it harder for eavesdroppers to glean sensitive information.
- Reduced Latency: Speed is vital in today's fast-paced digital world. The quicker the process, the better the user experience.
- Simplified Configuration: The configuration process is less complex, meaning organizations can save time and avoid potential pitfalls often linked with SSL management.
Another trend is the rise of post-quantum cryptography. With the potential capabilities of quantum computers loitering on the edge of our future, developing encryption methods that can withstand such power is critical. This push for quantum-resistant algorithms is becoming a priority among cybersecurity professionals.
"The next generation of SSL technology isn't just about keeping up with threats—it's about staying ahead of them."
The Shift Towards Automated Certificate Management
Automation is rapidly becoming the name of the game. As businesses grow and evolve, the ways they manage SSL certificates need to keep pace. Manual management is becoming increasingly burdensome, which can lead to human error and security vulnerabilities.
- Benefits of Automation:
- Efficient Renewals: Automated systems can prompt renewals before certificates expire, reducing the risk of downtime due to a lapsed certificate.
- Real-time Monitoring: Keeping tabs on certificate status can be tedious, but automated solutions offer real-time monitoring for any security issues or potential misconfigurations.
- Streamlined Processes: By automating tasks such as issuance, renewal, and revocation, organizations can focus on higher-level cybersecurity strategies without getting bogged down in administrative work.
Notably, Let's Encrypt, a widely adopted certificate authority, pioneered automated certificate management with its free SSL certificates, significantly impacting how businesses approach SSL management by simplifying the process and increasing adoption rates.
In summary, the future of SSL technology is geared towards incorporating sophisticated protocols and automation to provide robust security solutions. Understanding these trends equips cybersecurity professionals, IT specialists, and network administrators with the knowledge they need to implement and maintain secure communications amidst growing cyber threats.
The End
The conclusion serves as a pivotal section in grasping the full scope of SSL certificates and their relevance in today’s digital landscape. As we've explored various types of SSL certificates, along with the nuances of their management, challenges, and future outlook, this segment ties all the threads together, reinforcing the main ideas presented in the article. It encapsulates not only the technical insights but also the broader implications these certificates hold for security and trustworthiness in online interactions.
Summary of Key Points
- Diversity of SSL Certificate Types: We’ve examined how different SSL certificates—Domain Validated, Organization Validated, Extended Validation, Wildcard, and Multi-Domain—cater to varied needs. Each type provides unique benefits depending on the specific context in which they are deployed.
- Management Practices: Effective SSL certificate management is key. The emphasis on best practices and the criticality of timely monitoring and renewal processes cannot be overstated. A well-managed SSL environment significantly reduces risks associated with misconfigurations and vulnerabilities.
- Security Concerns: The potential vulnerabilities and risks, such as misconfigurations, were discussed extensively. Understanding these concerns is vital for IT professionals and cybersecurity experts to mitigate threats effectively.
- Future Considerations: Lastly, the exploration into future trends, like the adoption of automated certificate management and emerging protocols, hints at the evolving landscape of SSL technology and security measures in general.
Final Thoughts on SSL Certificate Selection
Choosing the right SSL certificate is akin to selecting the best lock for your door. Not all locks are created equal, and the choice depends not just on the door they will secure but also on the value of what lies behind it. For businesses, this translates into assessing factors like the nature of transactions, the sensitivity of data, and the overall website architecture. Ultimately, understanding your specific needs and the intricacies of available SSL certificates can guide you to make an informed decision.
The increasing importance of online security in our digitally driven world makes it imperative to invest time in properly understanding SSL requirements. Companies should not only consider immediate costs but also how the right certification can enhance customer trust and overall cybersecurity posture.
"In the realm of online safety, SSL certificates are more than just an added layer; they are the backbone of trust in digital transactions."
As businesses continue to grow their online presence, making an informed decision about SSL certificates stands as a critical investment in the future of their cybersecurity strategy.







